Welcome to the Future
So you’ve got determined to dive into web3, dApps, and the fascinating world of degenerate gamblers and obstinate builders of the web’s future.
Or, maybe you wish to take part on the enjoyable and experiment with new dApps, however are afraid of the quite a few methods you see folks dropping cash by falling for scams and malicious platforms. You are not tech savvy and consider you may be a great sufferer for the following rip-off.
Luckily for you, I am sharing the basics of on-line safety when utilizing crypto, DeFi, and web3.
This text will take you thru the steps it is best to take so as to be safer as you study and progress on web3. I will assume you are utilizing Google Chrome and Metamask, that are the preferred instruments proper now.
Newbie: Being Your Personal Financial institution
The benefit of web3 logistics is that you just set it as soon as and haven’t got to fret about it once more. You’ll acquire confidence to go additional on this new area in case you safe your accounts and funds. So, let’s begin with the basics and how you can safe every part.
1. Allow Two-Issue Authentication on All Accounts
2FA, or Two Issue Authentication, will prevent a number of hassle if hacks happen on the centralized apps you employ. When creating any account, go straight to settings and activate it. Right here’s an instance with a Twitter account, after going to “Settings”:
Step 1:
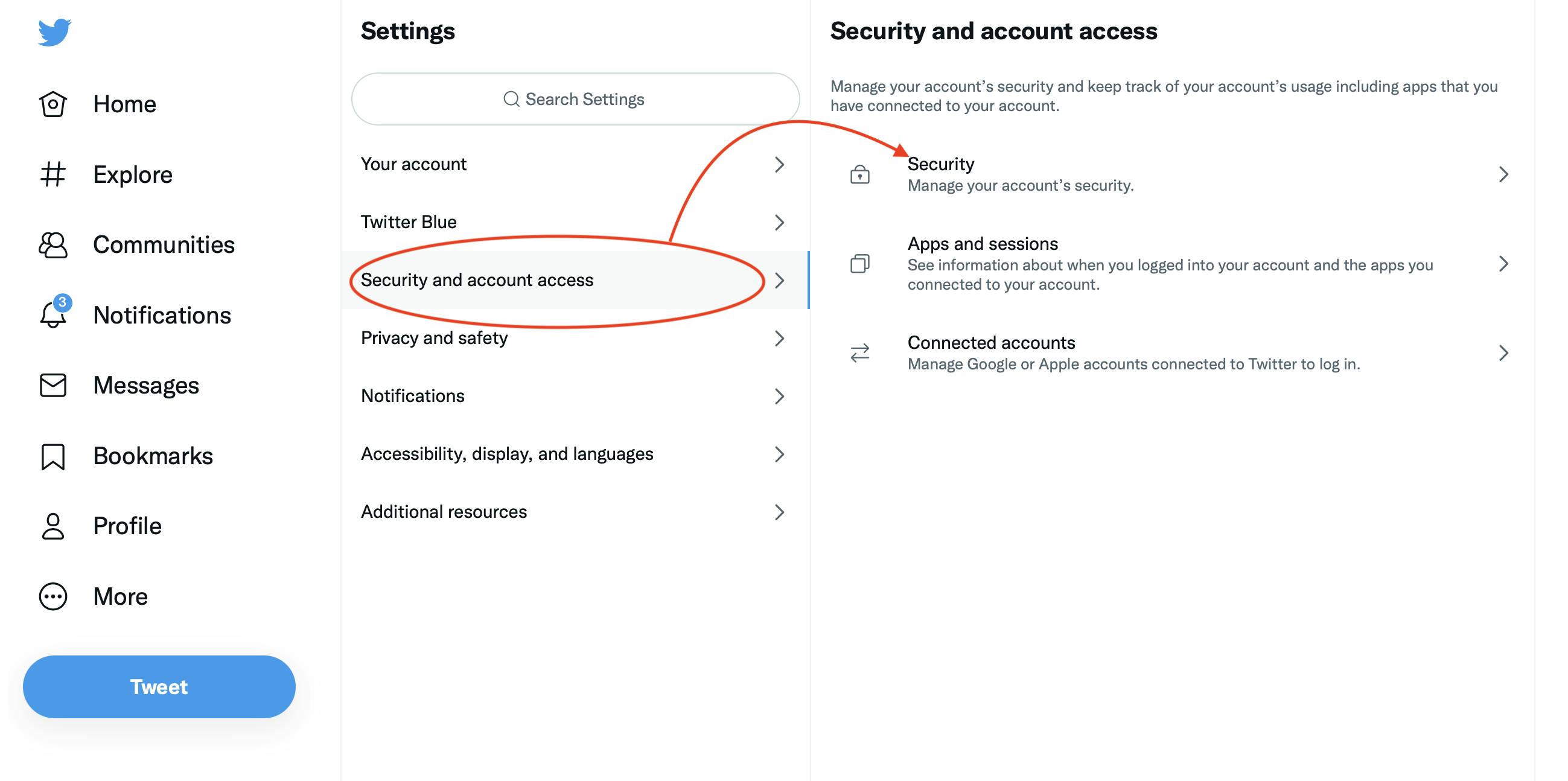
Step 2:
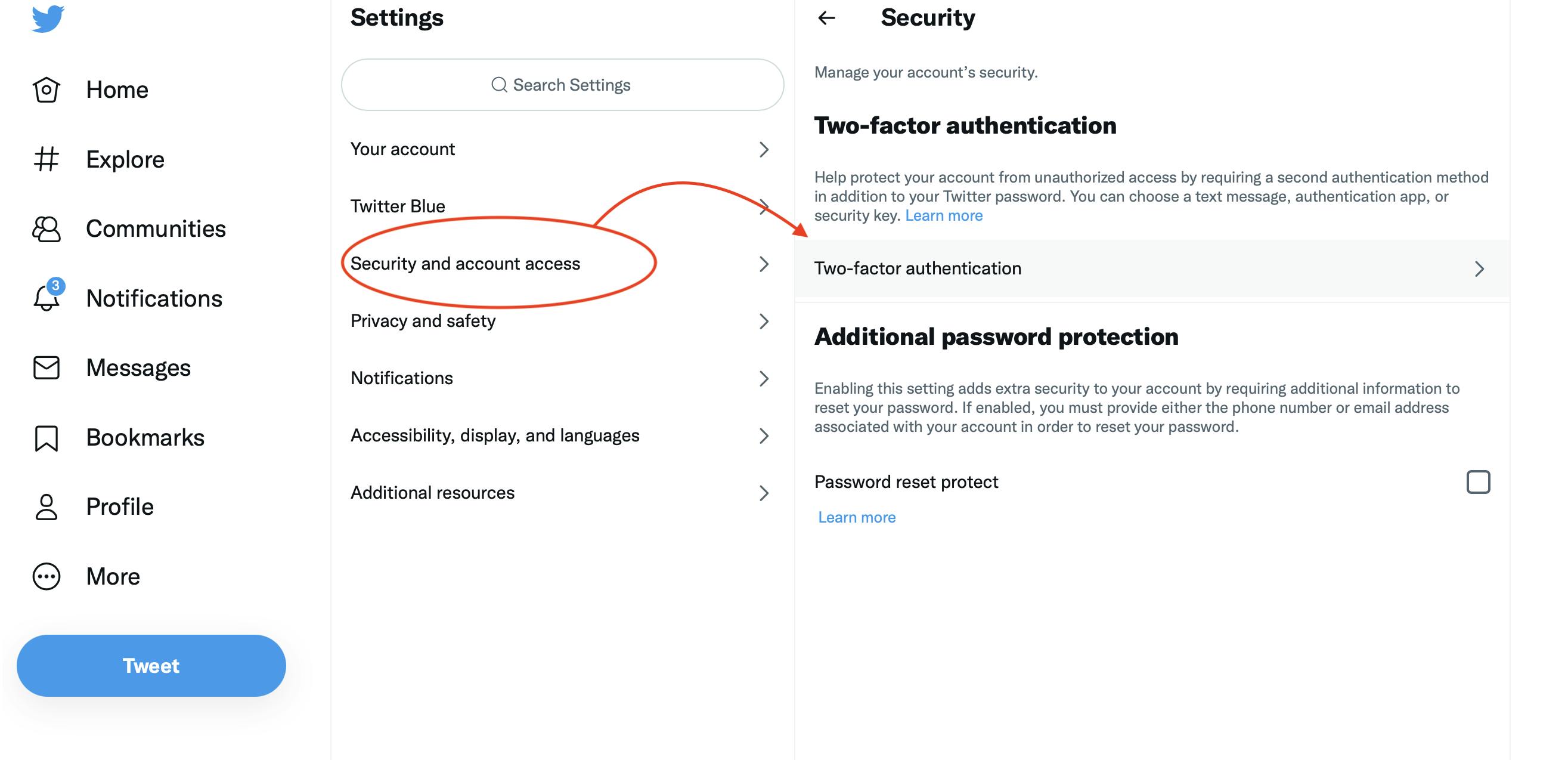
It’s important that you just don’t use a telephone quantity as a 2FA measure, as SIM card swapping is a typical observe amongst hackers these days. And sure, crypto customers are additionally focused.
As an alternative, you should utilize a 2FA app, which is able to generate a code for every time slot and let you log in after coming into the code. The preferred 2FA apps are Google Authenticator and Authy.
Step 3:
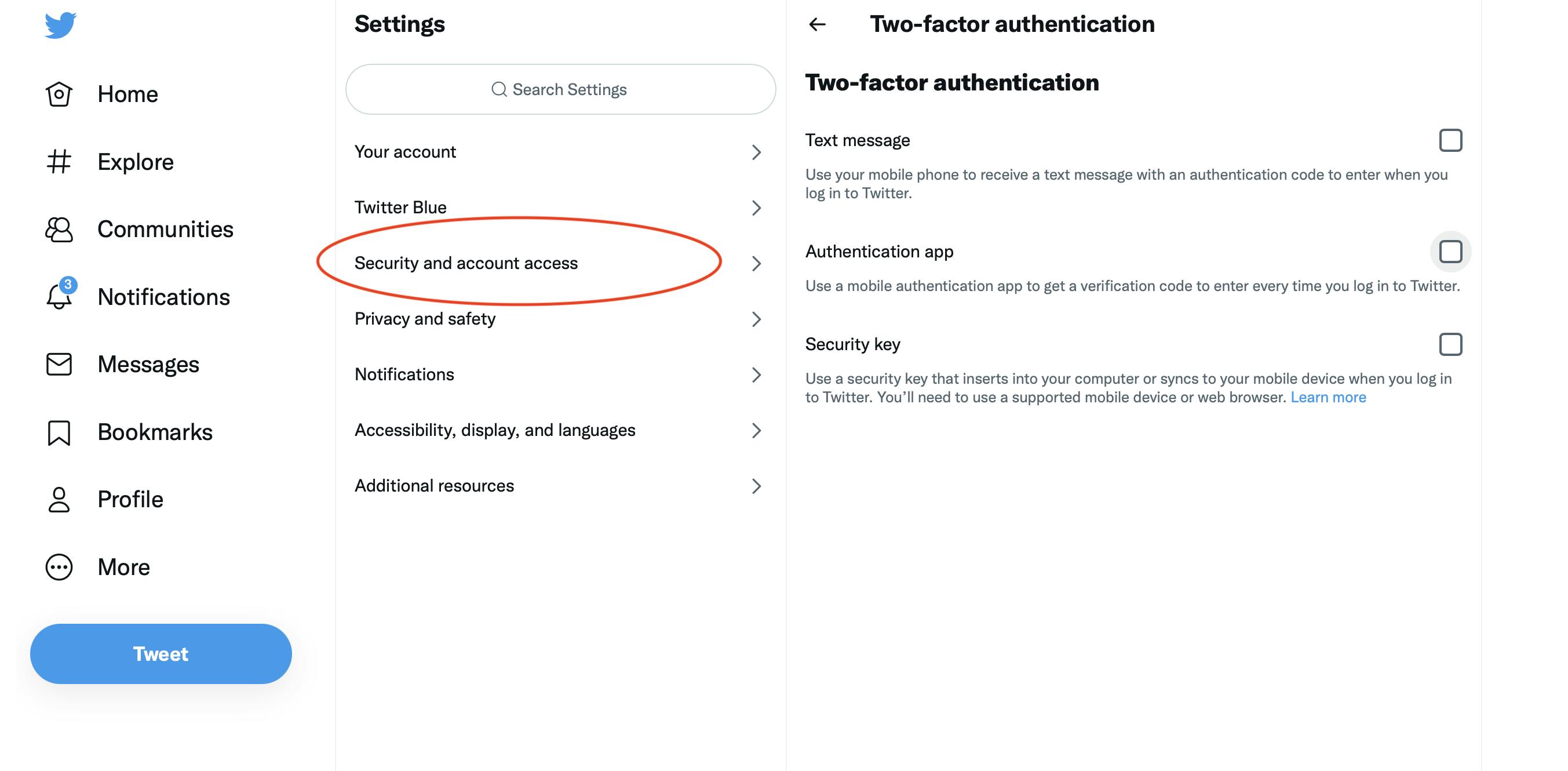
The very first thing it is best to do is shield your CEX account, which is the place you purchase and promote crypto for fiat.
The subsequent factor it is best to do is safe your social and discussion board accounts, the place you focus on cryptocurrency, to keep away from being hacked and granting entry to potential victims, particularly when you’ve got a big viewers.
Why Defend Your Social Accounts?
Having your social media accounts hacked may disqualify you from tasks in which you will have an interest. For instance, in case your deal with is whitelisted to mint a challenge, the hacker can change it and exchange it along with his.
Hacked social media accounts can be bought for pennies on the web. There’s a thriving marketplace for verified Twitter accounts with massive followings. Some specialised crypto web sites will promote your rank on some servers (which often grants you privileges equivalent to airdrops, token allocations, or being on a personal sale).
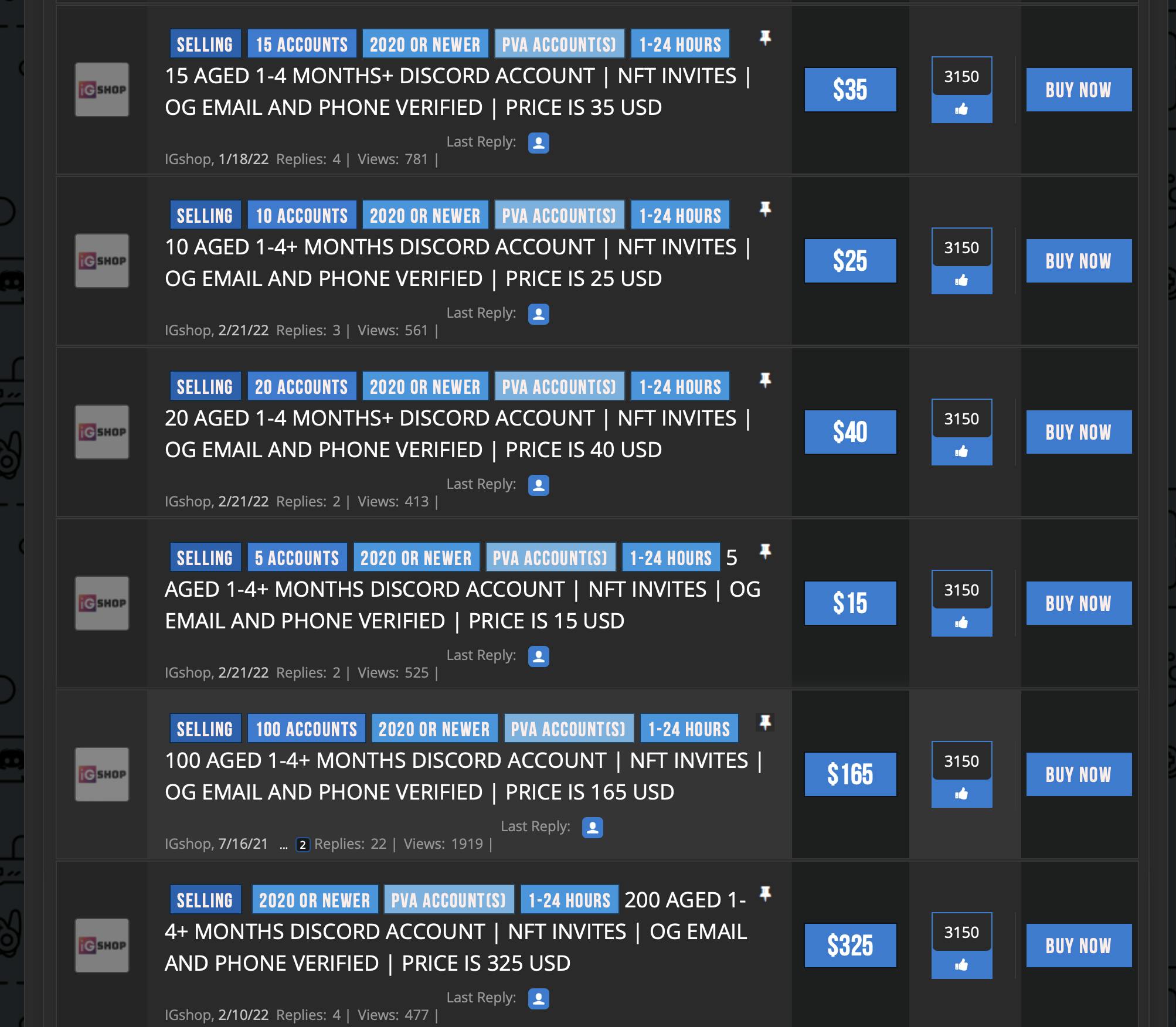
Sometimes, verified Twitter accounts are bought by scammers or NFT tasks with the intent of rug pulling (vanishing with folks’s cash after minting), and even cloning websites for profitable tasks. The scammers additionally want a pretend account on a centralized trade (CEX) to money out the cash.
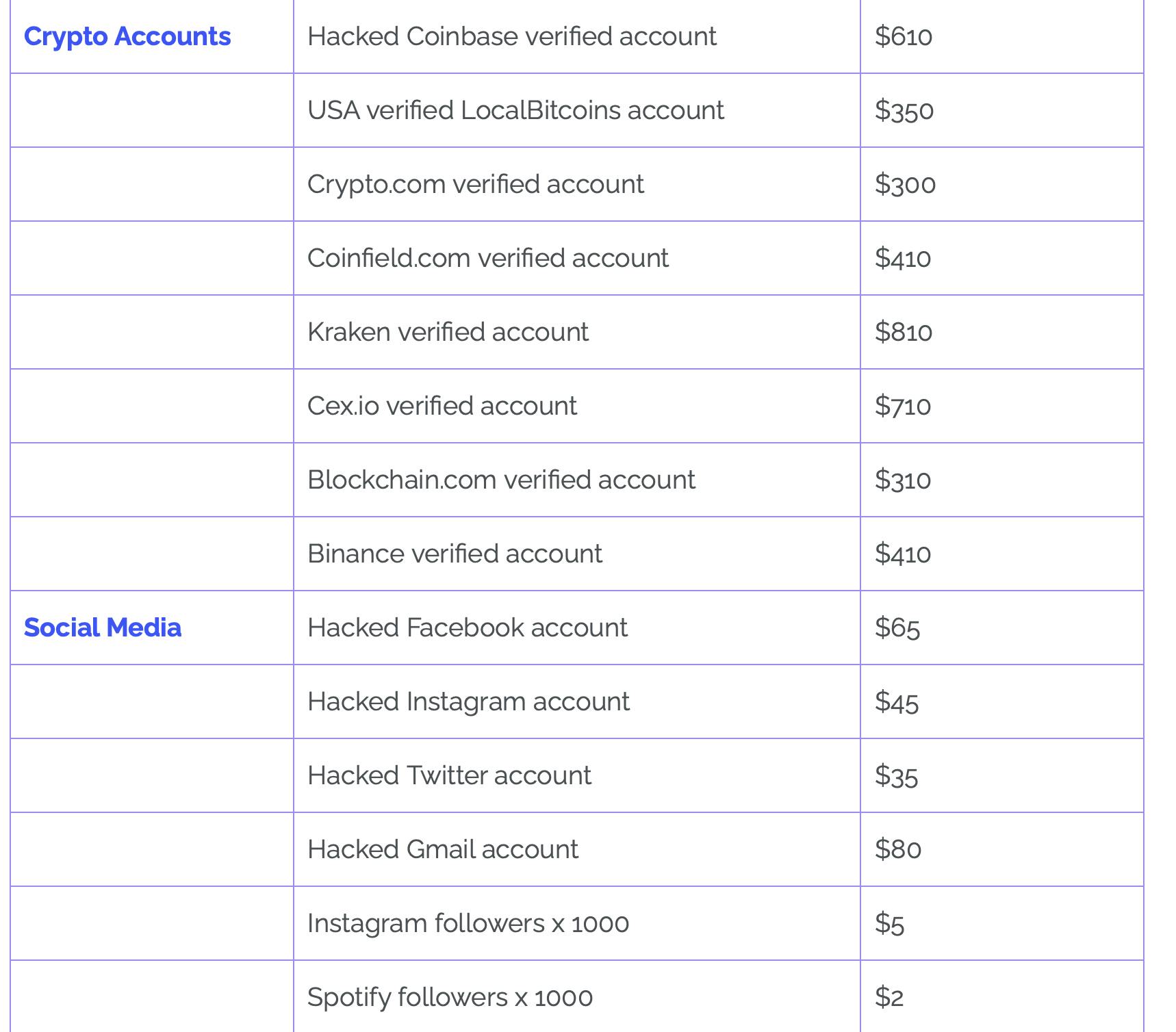
This screenshot is from this report. You may test it out if you wish to study extra.
I’ve misplaced rely of the variety of instances one in all these hacked accounts has talked about me on Twitter or added me to a pretend giveaway checklist. Individuals fall into the entice of associating being verified and having a big following with belief.
Scams Abound on Social Media
To keep away from falling into this entice, preserve this straightforward rule in thoughts: Nobody who has ever spoken to you’ll randomly provide you with something or select you to mint an unique challenge. No stranger with a big following will abruptly get up, and determine to slip into your DMs to ask if “your trades are going easily.”
Take into account the social media platforms you employ to debate crypto in danger, even when you do not have a big following. Web3 identification and evolution are inextricably linked to web2 instruments. Whenever you understand how invaluable they’re, you may wish to shield them simply as a lot as your cash.
2. Get a {Hardware} Pockets. Now.
Proper now, Metamask is the preferred pockets, and it’s generally the one choice for connecting to new tasks and dApps. Establishing Metamask will most probably be your first step in case you’re new to web3. Be cautious of cloned extensions and be sure you’re getting the actual deal by visiting the official website.
Most individuals on web3 make the error of misinterpreting Metamask for a pockets, when it’s merely a browser extension that acts as an interface between dApps and your precise {hardware} pockets.
Whether or not you just like the idea or not, a {hardware} pockets will probably be required in some unspecified time in the future. Trezor and Ledger are the preferred {hardware} wallets, and so they can be utilized along with Metamask as a further layer. After you affirm an motion on Metamask, it’s essential to affirm it bodily by urgent the gadget. In case you don’t bodily press that button, no funds will probably be despatched.
A Supplementary Safety Layer
Even in case you hook up with a malicious web site, you may be secure so long as you do not authorize something along with your {hardware} pockets. And not using a {hardware} pockets, your Metamask might be hacked and begin being remotely monitored by a hacker or a script.
In fact, these safety layers will probably be ineffective in case you signal on to a suspicious web site that you’ve got by no means seen earlier than. However, don’t fear. We’re right here to take you to the following degree. However first, lets safe that {hardware} pockets?
3. Mnemonic Phrase 101
A non-public key will probably be used to safe your cryptocurrency pockets. This non-public secret is saved in your {hardware} pockets and tracks all your actions. It’s often a mnemonic phrase of 12 to 24 phrases.
This non-public key allows the person to revive any current pockets on any gadget within the occasion that the bodily pockets is misplaced or destroyed. As well as, they’re the weakest hyperlink in pockets administration.
The key key should be saved hidden always. You shouldn’t give it to anybody or publish it on any web site. Be cautious of internet sites or customers who request that you just “resync” or “join” your pockets by coming into your non-public key. Your pockets won’t ever have to be resynchronized. That’s the reason blockchain know-how exists.
Protecting Your Non-public Key Protected
Some cryptocurrency customers have their wallets emptied with out understanding the way it occurred. They by no means informed anybody their phrase. Till they understand they’re internet hosting it themselves…within the cloud or on their pc.
Your seed phrase mustn’t ever be uncovered to the web, a keyboard, or every other digital gadget that has beforehand been related to the web.
You shouldn’t take a screenshot of your seed phrase, print it, or retailer it wherever, particularly in your pc.
You must write it down, or on the very least, memorize it, and put it aside someplace.
Remember that anybody who finds this piece of paper will be capable to recuperate your pockets and switch your funds. No person ought to know the place your seed phrase is saved, not even your spouse.
If this piece of paper is destroyed for some cause, merely ship your funds to a model new pockets as a result of relying solely on a tool is, properly, form of dangerous.
4. Do not Click on That Hyperlink, or Avoiding Phishing
As a result of you will have a cryptocurrency pockets, you’ll most probably be focused by phishing emails and hyperlinks. In case you obtain an e-mail advising you to obtain your crypto pockets’s up to date software program as quickly as attainable, do not achieve this. First, examine the model’s web site, then their weblog or social accounts to see if any updates have been introduced.
To keep away from phishing emails, an excellent piece of recommendation is to create a brand new e-mail deal with that you just’ll solely use for crypto, and by no means click on on any hyperlink despatched to you, particularly any hooked up recordsdata. NEVER.
Hooked up Recordsdata
Hooked up recordsdata in emails can comprise malware that’ll hack your pc and try to steal your funds. In fact, in case you use a {hardware} pockets, you will have added an additional layer of safety, however there are a number of exploits accessible that you just’ll find out about on the medium and superior ranges.
As a basic safety precaution, do not open any attachments despatched to you by an unknown e-mail, and do not set up something with a .exe or .scr extension despatched to you by a stranger.
Search Engines and Browsers
One other piece of recommendation is to keep away from utilizing Google as a search engine. In case you use Google as a search engine, you may discover clones and phishing websites on the primary web page as a result of scammers pay to rank on the primary web page. You may change the settings of any browser to make use of another like DuckDuckGo or Ecosia.

Clone websites exist as a result of the malicious actors behind them are conscious that crypto customers’ funds are linked to a browser extension, which is technically susceptible to hacking. Earlier than DeFi went mainstream, there have been clones of banks’ web sites.
Compartmentalizing Your On-line Exercise
Utilizing various engines like google not solely improves the accuracy of outcomes, but additionally eliminates the vast majority of rip-off web sites. The last word hack is to separate your actions: Use one browser for analysis and one other for Metamask solely.
Bookmark Hyperlinks
Discovering the official Twitter account for no matter dApp you are on the lookout for (OpenSea, LooksRare, and many others.) and bookmarking the hyperlink is frequent observe. This was the very first thing I realized after I arrange my Trezor for the primary time.
Flip Off Non-public Messages on Discord
Flip off non-public messages in case you’re utilizing Discord to observe some tasks.
Scammers posing as directors will ask in your seed phrase (a fairly apparent rip-off, nevertheless it nonetheless works) so as to “Join your pockets,” or will ship you clone websites or phishing hyperlinks. Some even name themselves “Bulletins” to trick you into considering they are a channel notification fairly than a personal message.
The Good Bots Are Scammers
Do you will have an issue along with your pockets? Have been you hacked? Did you fall sufferer to a rip-off and are actually powerless? In case you point out it in public, you may get the great Metamask, Belief Pockets, or Coinbase assist in your mentions or non-public messages providing to assist. Don’t belief these accounts on social media.
Sure, as soon as once more, they’re scammers. I’ve seen folks on Twitter speak about getting scammed, but falling for one more rip-off once more. It is heartbreaking. So, let me state this as soon as once more: Your mom was appropriate, do not belief strangers on the web.
As soon as your funds are depleted, they’re gone for good. There are some subtle methods to cease the draining; for instance, if the hacker runs out of gasoline.
Whereas there are white hat hackers who can finally make it easier to keep away from an exploit in your pockets, the vast majority of folks reaching out to you on social media to supply help want to benefit from your desperation in such a state of affairs.
Replace Your Software program
This needs to be commonplace observe for everybody, nevertheless it’s particularly vital when coming into web3. Hackers will take the shortest route by exploiting your software program flaws. Updates embody patches for vulnerabilities, in addition to elevated safety.
Software program flaws are in every single place, and the one option to detect them is after they’ve been exploited. Consequently, in case you obtain a notification of a software program replace on the gadget wherein you employ a crypto-wallet, set up it straight away fairly than losing time worrying about how lengthy it’ll take.
Frequent updates point out that the crew is conscious of vulnerabilities and is working rapidly to patch them. Within the superior degree of this text, you’ll dig deeper into the Metamask code supply to search for suspicious exercise, however updating your software program is among the simplest methods to keep away from being hacked and dropping your cash and valuable NFTs.
You’re all set when you’ve secured your funds, protected your social accounts, and ensured that they will not be wiped by a phishing hyperlink. It is time to transfer on to the following degree of verification, the place you may discover ways to confirm the data supplied by third events.
5. What to Keep away from
Whereas utilizing crypto and dApps, it is best to keep away from sure actions. These behaviors must also be prevented on web2, notably when utilizing monetary instruments or speaking with authorities. Many customers are unaware of this or are unconcerned in regards to the WiFi community they’re utilizing whereas performing delicate actions.
Being an energetic web3 person means changing into conscious of threats and risks that you weren’t beforehand conscious of. In case your bank card is compromised, your insurance coverage firm and financial institution may help. Nevertheless, in case you lose funds from a non-custodial crypto-wallet, you gained’t be capable to recuperate them.
The 2 most vital issues to keep away from are performing delicate actions on insecure networks and believing every part you see on the web.
Public WiFi
Airports, cafés, and even faculties present public hotspots for his or her guests, and since they entice numerous folks, they’re incessantly focused by malicious third events searching for delicate data.
WiFi networks which are open to the general public could be accessed by virtually anybody. Your communications and data could be monitored and even altered. To realize entry to your information much more simply, some malicious actors launch pretend public WiFi networks masquerading as institutions.
Merely keep away from delicate actions, equivalent to connecting to your checking account or logging into any app when utilizing public WiFi, and do not use cryptocurrency on it.
Don’t Belief, Confirm
Some tasks’ servers on Discord have been hacked previously, saying pretend mintings or giveaways, inflicting customers to lose funds. Though some customers instantly acknowledged hacks resulting from differing syntax and writing fashion from that of the founders, many weren’t in a position to, leading to getting scammed.
Whenever you see one thing surprising or uncommon that requires you to spend your cash or join your pockets, examine the challenge’s different social accounts. Occasions are often introduced upfront, so see if any official bulletins have been made and what persons are saying on social media.
This is among the most vital ideas to know when navigating web3: Do not belief, confirm.
6. Set a Metamask Throwaway Account
When interacting with a dApp or a contract for the primary time, it’s frequent observe to make use of a disposable Metamask account. This account is totally separate out of your important {hardware} pockets, and can shield you in case you work together with a malicious contract or actor.
However what if you wish to declare an airdrop based mostly in your present holdings, for instance? To say it, it’s essential to use a pockets that comprises some invaluable NFTs or cash. That is if you should be cautious.
7. Discovering Addresses on Etherscan
Etherscan is a unbelievable instrument and, for my part, the perfect block explorer accessible. Whenever you’re about to signal your first transaction on a dApp, copy the deal with you’re about to work together with and seek for it on Etherscan. You’ll instantly know if the deal with belongs to the challenge wherein you are trying to take part. For instance, after I was about to mint a Tubby Cat, Etherscan displayed this deal with.
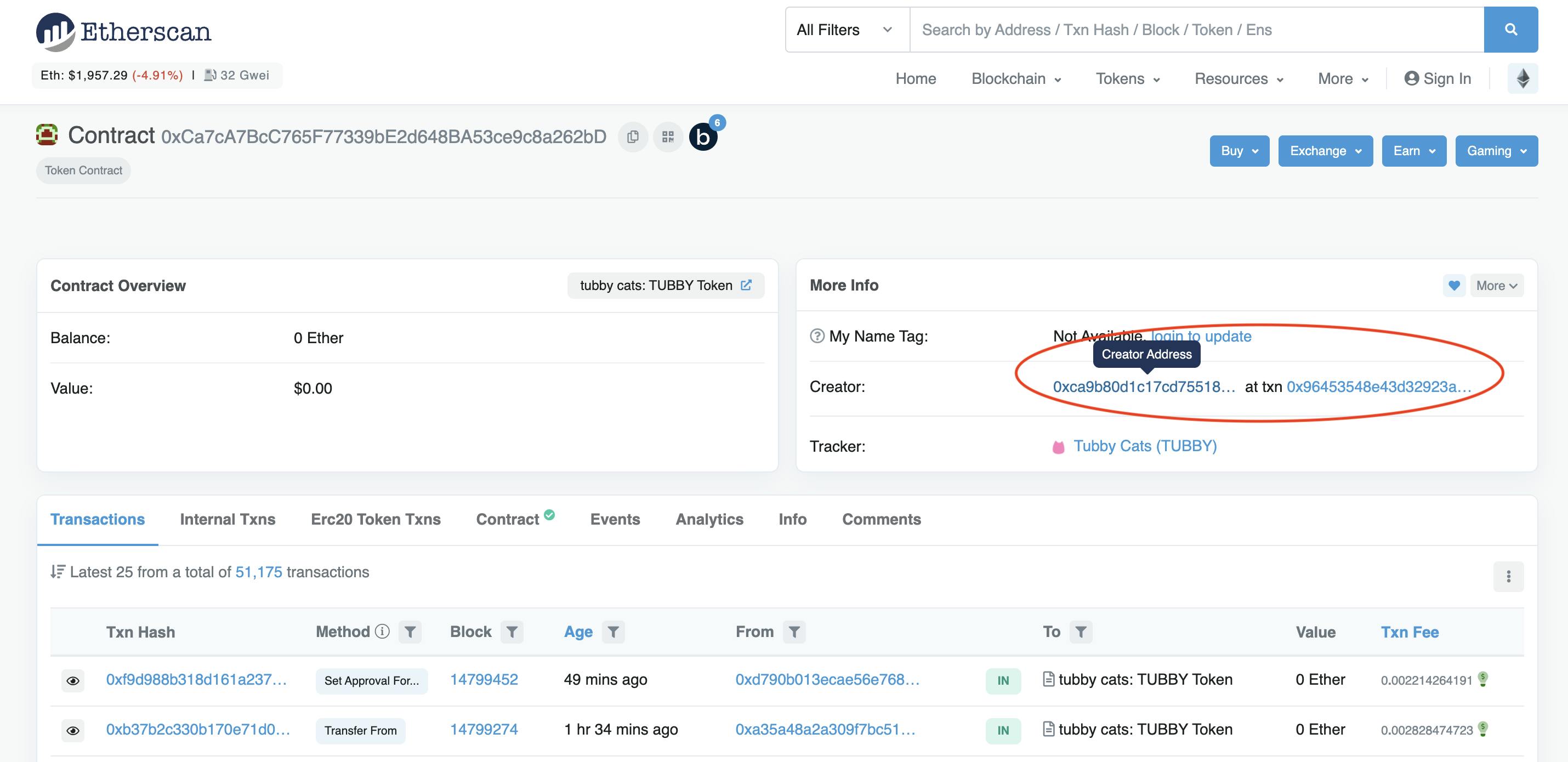
You can even evaluate the deal with to these listed within the challenge’s documentation; on an NFT platform like OpenSea, or on the challenge’s Discord server.
There’s rather a lot to study from trying on the creator’s on-chain exercise. The place does the funds come from? Are they related to rug pulls? Breadcrumbs could also be helpful within the analysis section to simply chart transactions.
You needn’t grasp these investigation expertise to start your web3 journey, however they’re choices for the long run if you wish to study extra about researching with explorers.
Including Trusted Addresses to Your Contact Listing
As soon as you’ve got discovered the best deal with to work together with regularly, add it to your Metamask contact checklist.
This not solely saves you time, nevertheless it additionally prevents Metamask’s random rewriting hacks.When the hacker, or a bot, detects a person is about to switch funds, they attempt to intercept it.
Assume you wish to transfer some cash to a different pockets or put them in a liquidity pool. When the script detects a switch, it hacks your Metamask by pasting a distinct deal with instead of the one you copied.
At the next degree, you’ll discover ways to confirm the place Metamask is getting its information from, however for now, making a trusted contact checklist will suffice.
This activity could take a while, however in case you full it as quickly as you obtain the trusted deal with from Etherscan, it’ll be finished. Until, after all, the trusted deal with adjustments, wherein case you’ll see a random deal with. You’ll solely must confirm its legitimacy earlier than approving something.
8. Studying Transactions
One other ability it’s essential to study to remain secure on the web is to not signal blindly. You have to pay attention to the actions you’re about to approve. There’s no {hardware} pockets that may prevent in case you use it to signal any transaction that comes up.
You may cancel a transaction; for instance, in case you click on on “Join pockets” however the transaction information exhibits “Approve limitless spending of funds”, that’s most probably not an excellent signal.
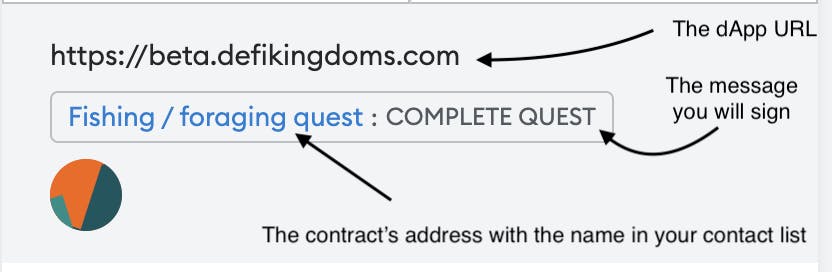
Be Conscious of How A lot Approval You’re Giving
You may change the spending permission for every transaction. By no means give permission for greater than you propose to make use of. You may at all times change it later.
9. Verifying a Token Handle
As a result of anybody can create a pretend token and distribute it on a decentralized trade (DEX), the token deal with should be verified on Etherscan. To find a token deal with, use Etherscan or one other respected web site equivalent to Coinmarketcap.
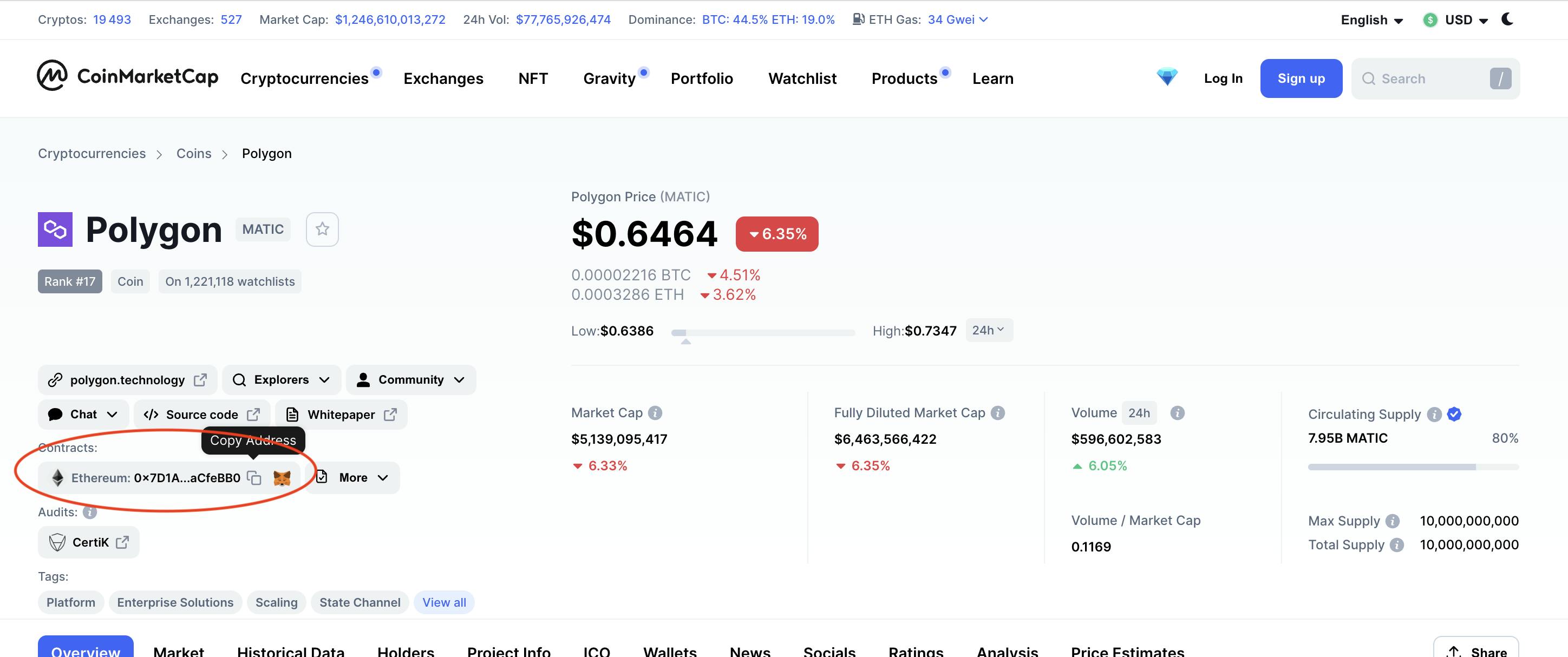
The token deal with permits you to add it to your pockets and to the DEX lists if it hasn’t been added beforehand.
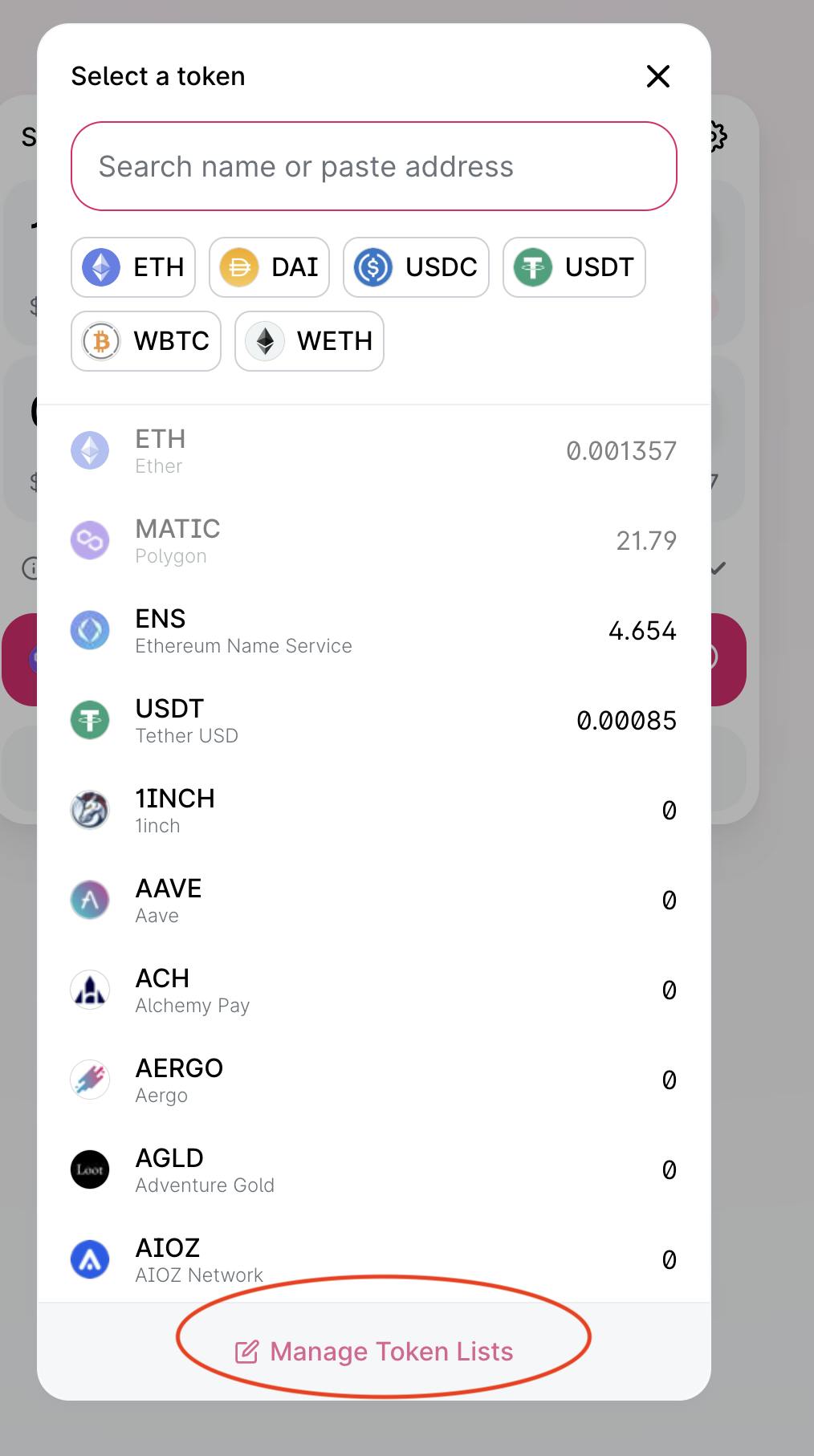
In case you’re swapping tokens for the primary time on a brand new DEX, make certain to work together with the best ones this fashion.
Superior: Studying Contracts, Audits and Revoking
Now that you just perceive what you are signing and are a bit extra aware of web3, it is time to beef up your safety.
This degree could be attained by additional verifying duties and systematically revoking what you are not utilizing. Sensible contracts rule web3, and we’ll train you all about them.
10. Sensible Contract Verification
Nearly all of your web3 exercise consists of approving good contracts along with your pockets. Nearly all of web3 vulnerabilities are present in good contracts, that are being exploited.
As a result of the vast majority of web3 is open supply, exploits are rapidly recognized by the group. The contract is then revoked by customers whereas it’s being patched.
It needs to be famous that there aren’t any easy strategies for figuring out the safety degree of any contract earlier than an exploit happens. As is at all times the case, vulnerabilities emerge after an assault.
Though open supply code and transactions assist the group reply faster, there’s a downside: Anybody watching the exploit in progress could determine to copy it as properly. For this reason some codes are now not open supply, however as a substitute, are audited by trusted third events. Let’s take a look at how one can validate the contract you’re interacting with.
Discover the Contract
Any good contract, like your pockets, is related to an Ethereum deal with. In case you use a {hardware} pockets, click on on it and look ahead to the Metamask pop-up to ask for approval. As an alternative of accepting, copy and paste the deal with.
You can even discover contract’s addresses on aggregators, like DeFiLlama.
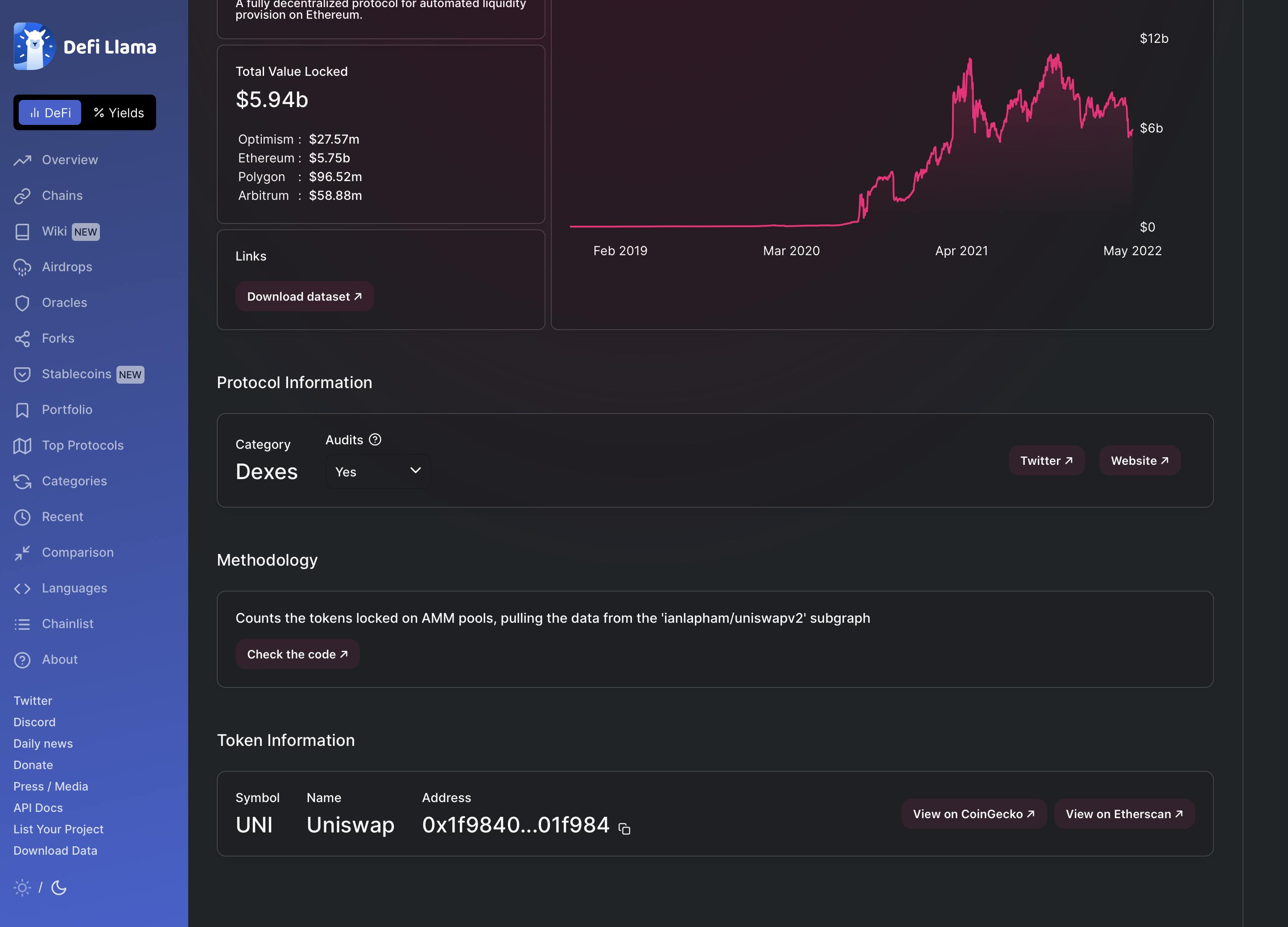
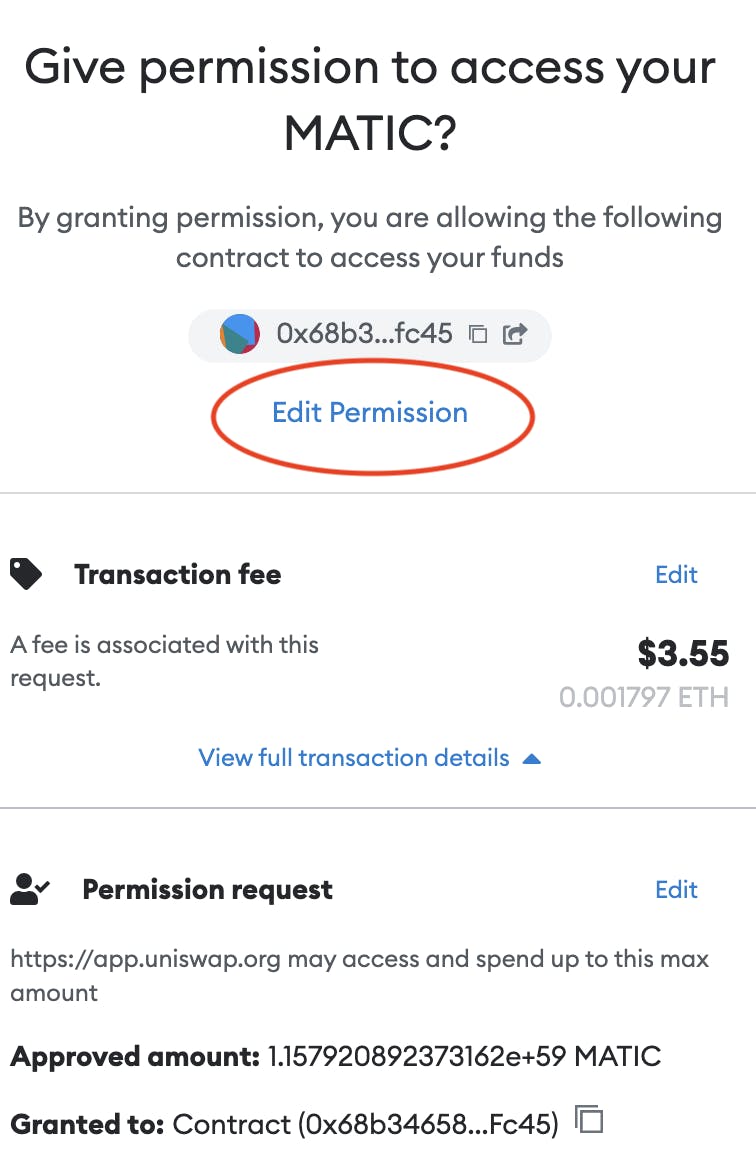
After you have the contract’s deal with, enter it on Etherscan. On this instance, we’ll take a look at the Uniswap contract. Let’s double-check who we’re giving permission to spend our MATIC with.
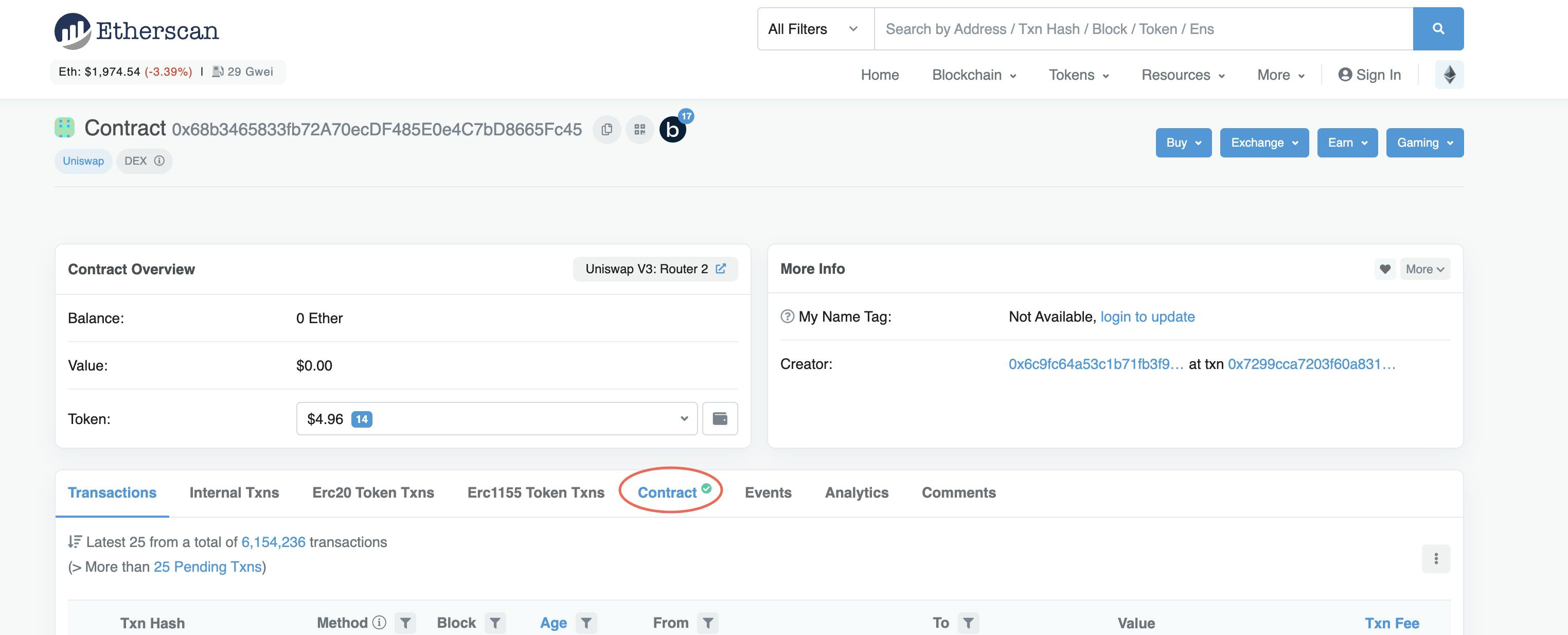
The very first thing you see is that the contract is verified, which signifies that solely the contract’s homeowners can modify it.
Verify the Contract
The Uniswap contract is open supply on this case, that means, any vulnerabilities or malicious capabilities could be found by anybody. Even when you do not know how you can interpret the code, a fast web search will let you know what you are stepping into.
Have a look at the capabilities outlined within the contract in case you’re feeling nerdy and keen to dig into the code. What precisely are we on the lookout for? Any operation that:
-
Permits entry to a selected token,
-
Doesn’t allow us to withdraw funds from a liquidity pool,
-
Masquerades as a deposit, however sends our tokens to a hacker’s pockets.
Look particularly for the ‘SpendWalletWETH’ operate (that is for WETH, however may apply to every other token) and what causes it.
In case you’d fairly die than learn a single line of code (comprehensible), you should utilize DeFiSafety or every other third-party companies that assess and publish the dangers related to a challenge, dApp, or contract.
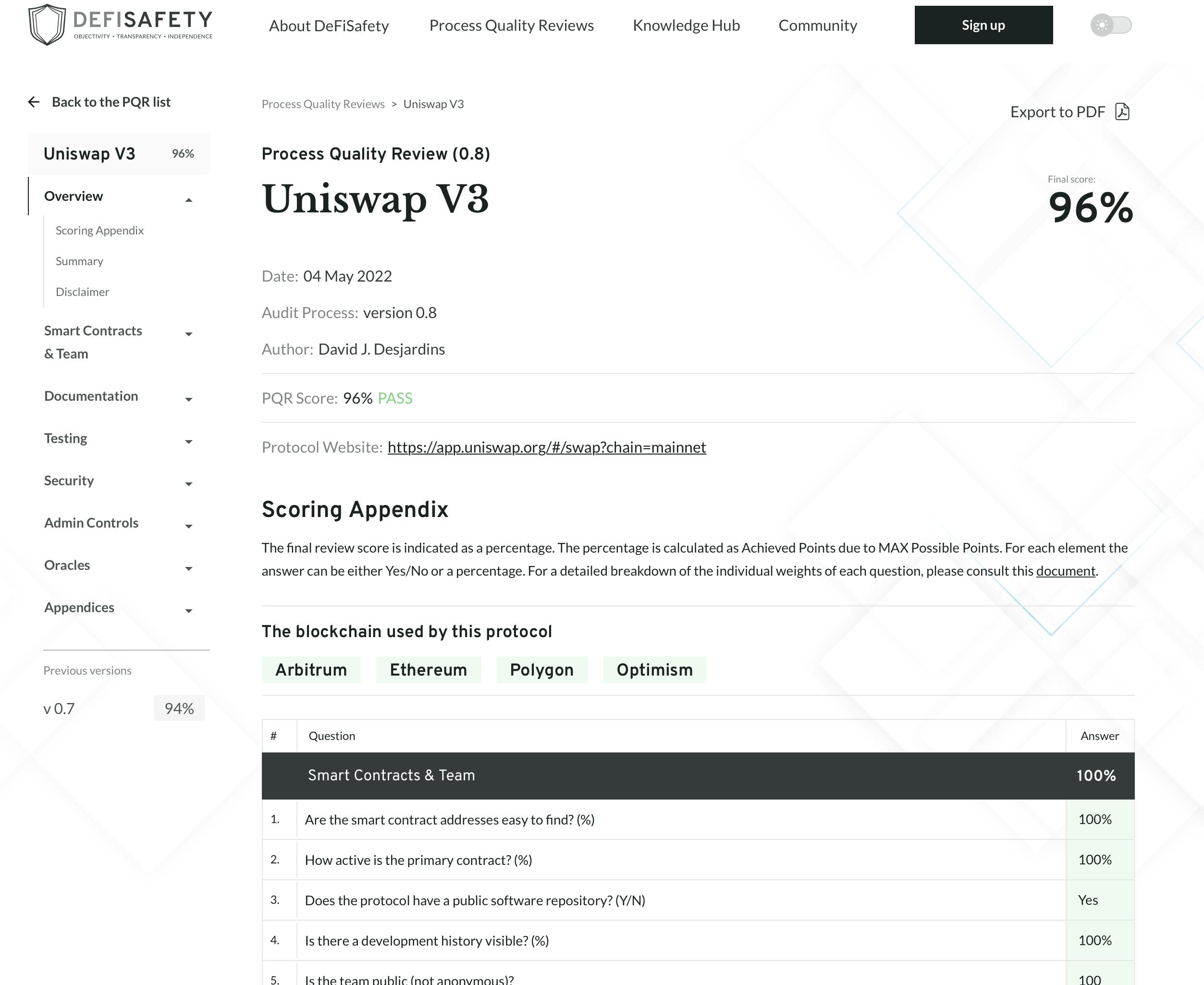
It is best to not depend on your self, as a substitute look into what third events and builders are saying a few protocol you wish to attempt. The better the transparency of the documentation and audits, the higher.
11. Verifying Metamask Information
Day-after-day, new strategies of stealing property are rising, and this one is feasible even in case you use a {hardware} pockets. On this case, the thief targets homeowners of huge quantities of cryptocurrency. The funds are stolen by intercepting a transaction and altering the recipient’s deal with. Keep in mind how I stated it is best to make a contact checklist? That is the rationale why.
Whenever you wish to switch funds between wallets and do not take note of the transaction particulars earlier than signing along with your {hardware} pockets, the hacker injects a code that rewrites the transaction, altering not solely the deal with, but additionally the quantity so as to drain the pockets in a single transfer.
In case you aren’t aware of the Metamask code base, the hack isn’t troublesome to identify in its settings. Navigate to Chrome’s settings, choose “Extensions”, and allow “Developer Mode”.
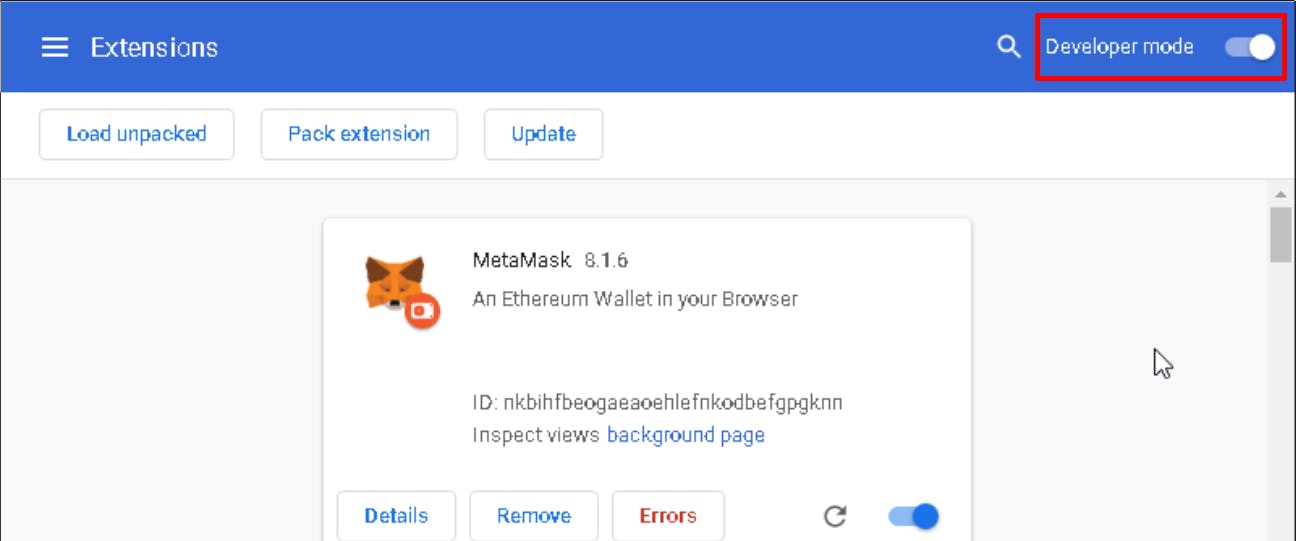
If the supply is Chrome Net Retailer, you’re effective.
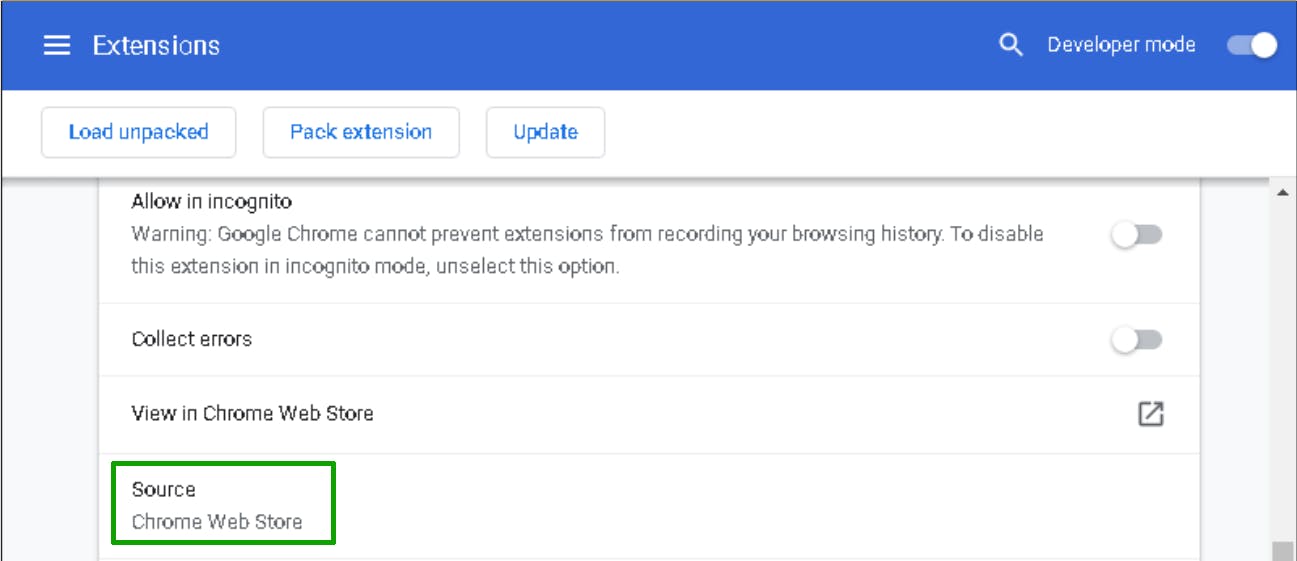
When unsure, double-check and at all times use Net Retailer extensions. Learn transactions rigorously earlier than signing, and cancel something that seems suspicious.
12. Revoking Permissions
You have to approve good contract permissions so as to work together with dApps. You’ve got found that good contracts let you change the quantity you approve, and now you may develop a brand new behavior for good pockets hygiene: Revoking token approvals.
Token approvals are an assault vector for a wide range of scammers and hackers who will exploit code flaws to empty funds (this occurred to Wormhole. It’s because the default approval is often set to “limitless”, and customers do not hassle to alter it. Make a behavior of reviewing your approvals on a month-to-month foundation and discarding these you do not intend to make use of.
Revoking With Community Explorers
Protecting monitor of your current approvals is straightforward. Merely navigate to the “Approval” part of your community explorer, equivalent to Etherscan, BSCScan, or Polygonscan.
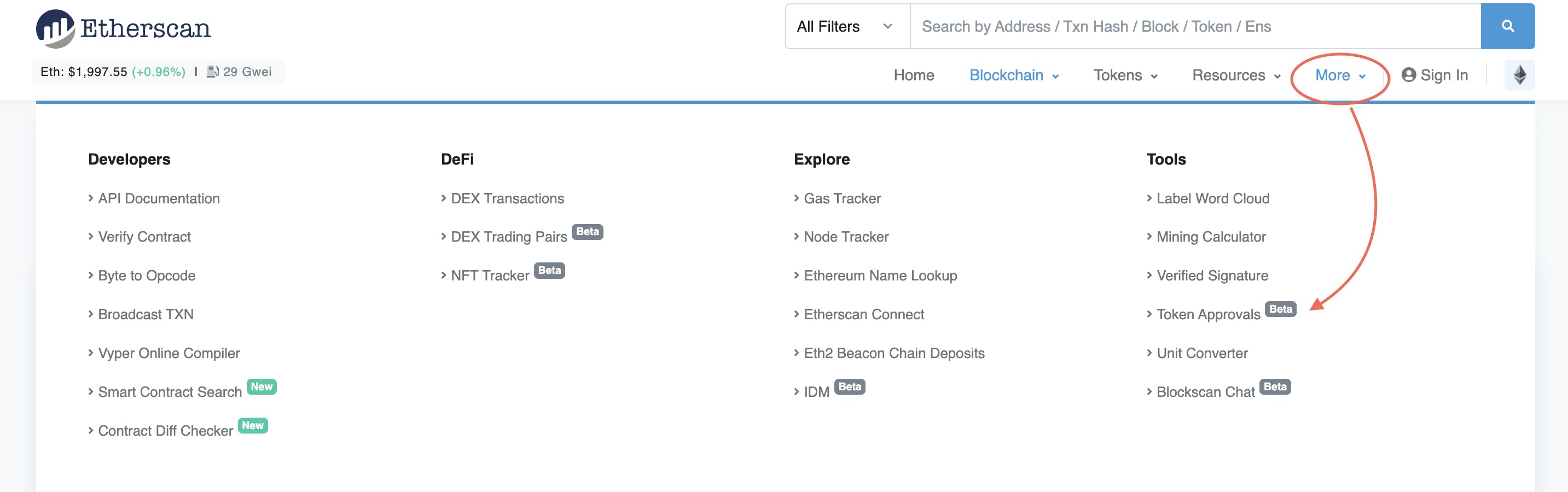
Join your pockets and revoke any token approval. You can even use websites like Revoke, Unrekt and Approved Zone.
Conclusion
Navigating web3 in its early levels safely requires a shift in habits. With a purpose to shield their funds, customers should be cautious navigating web3 as a result of its use entails the switch and manipulation of cryptocurrencies, in addition to the irreversible nature of the transactions.
Utilizing DeFi instruments and collaborating in web3 tasks can earn you some huge cash. However equivalently, a massive sum of cash can be misplaced resulting from a single error.
In web2, customers create content material and hand over possession to some centralized organizations that revenue from it. In web3, buying energy, possession, and wealth comes with having the ability to take enormous obligations and accountability.
This weblog is part of the Hashnode Web3 blog, the place a crew of curated writers are bringing out new sources that can assist you uncover the universe of web3. Verify us out for extra on NFTs, blockchains, and the decentralized future.









